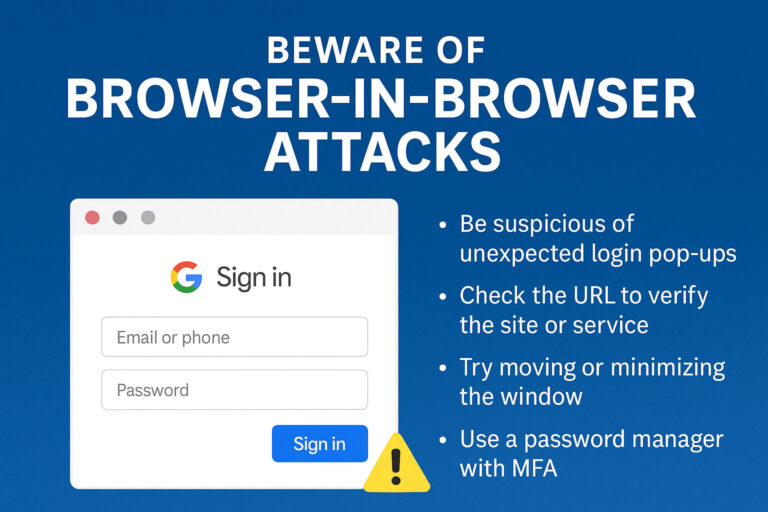
Why It’s Essential for Modern Cybersecurity
In today’s digitally-driven world, the traditional perimeter-based security model is no longer sufficient. With the rise of remote work, cloud services, and sophisticated cyber threats, organizations need a more robust and flexible approach to safeguarding their data and systems. This is where the Zero Trust model comes into play. At Citynet, we understand the importance of staying ahead in the cybersecurity landscape, which is why we deploy advanced Zero Trust solutions, such as Cisco DUO, for our customers.
What is Zero Trust?
Zero Trust is a cybersecurity model that operates on the principle of “never trust, always verify.” Unlike traditional security models that trust users and devices within the network by default, Zero Trust assumes that every attempt to access the network, whether from inside or outside, is a potential threat. This means that every access request is thoroughly vetted before granting access.
Core Principles of Zero Trust
Verify Every Access Attempt
Zero Trust requires continuous verification of all users and devices trying to access resources. This verification process includes multi-factor authentication (MFA), device health checks, and strict access controls.
Limit Access to the Minimum Necessary
With Zero Trust, users are granted the least amount of access they need to perform their tasks. This minimizes the potential damage in case of a breach by limiting the attacker’s access to sensitive resources.
Assume Breach
Zero Trust operates under the assumption that a breach has already occurred or will occur. This mindset helps organizations to be proactive in monitoring and responding to potential threats.
Micro-Segmentation
This involves dividing the network into smaller segments, each with its own access controls. By isolating different parts of the network, Zero Trust can contain breaches and prevent them from spreading.
Why Zero Trust Matters
The shift to remote work and cloud services has blurred the traditional network perimeter, making it easier for cyber attackers to find vulnerabilities. Zero Trust addresses this challenge by ensuring that security is not dependent on the network perimeter but is built into every access request and interaction within the network. This approach significantly reduces the attack surface and enhances an organization’s overall security posture.
Citynet and Cisco: A Partnership for Enhanced Security
At Citynet, we are committed to providing our clients with cutting-edge cybersecurity solutions. Our long partnership with Cisco, a global leader in networking and cybersecurity, allows us to implement the most advanced network security solutions. Cisco’s Zero Trust solution, Cisco DUO, is a key component of our security offerings.
Cisco DUO helps organizations implement Zero Trust principles by providing robust multi-factor authentication, device visibility, and adaptive access policies. It ensures that only trusted users and devices can access your applications, regardless of their location. With Cisco DUO, organizations can protect their data and applications from potential breaches, enhance user productivity, and comply with regulatory requirements.
Adopting a Zero Trust model is no longer optional; it’s a necessity in today’s complex and ever-evolving cybersecurity landscape. Contact Citynet today for comprehensive Zero Trust solutions that will help you safeguard your organization’s critical assets and data.