
Unified Access Security
Secure access to your applications and data, no matter where your users are – on any device – from anywhere.
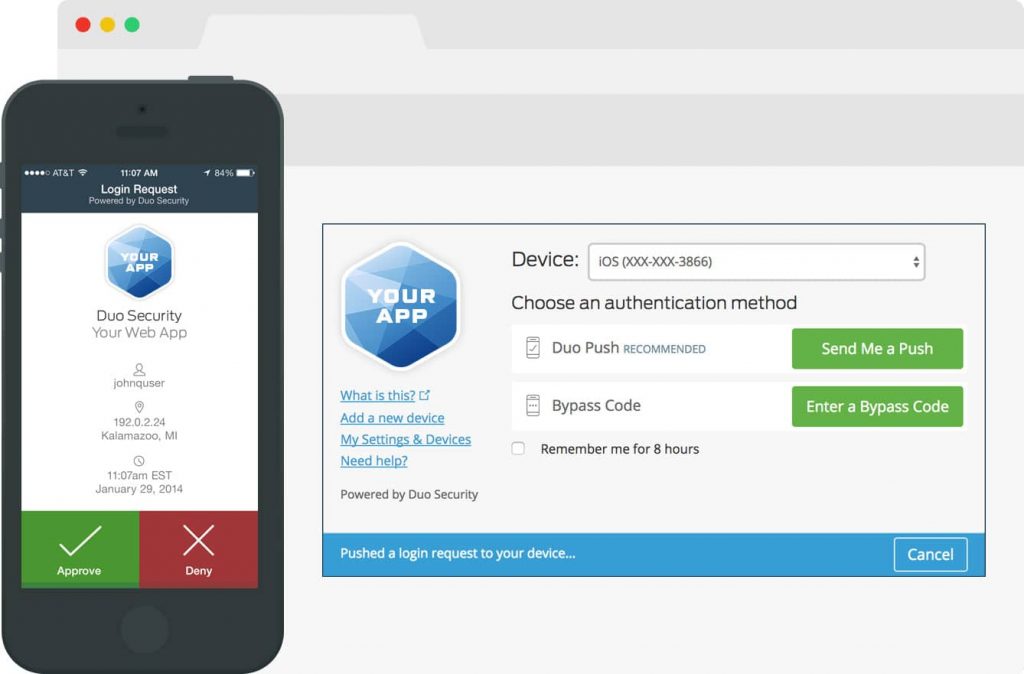
Multi-Factor Authentication (MFA)
Gain Trust in Users
Make sure your users are who they say they are. Verify users’ identities with Duo’s strong two-factor authentication – before granting access to applications – to protect against phishing and other access threats. This is the first step toward a zero-trust security platform.
- Wide variety of authentication methods
- Easily enroll and manage users
- Quickly deploy, at scale
- Assess user risk with phishing simulation


Endpoint Visibility
Gain Trust in Devices
When paired with strong identity verification, Duo allows you to check that your users’ devices meet your security standards before granting them access; safeguarding against vulnerable or potentially compromised endpoints.
- See, track and report on all end user devices from a single dashboard
- Monitor and identify risky devices
- Identify corporate vs. personal devices
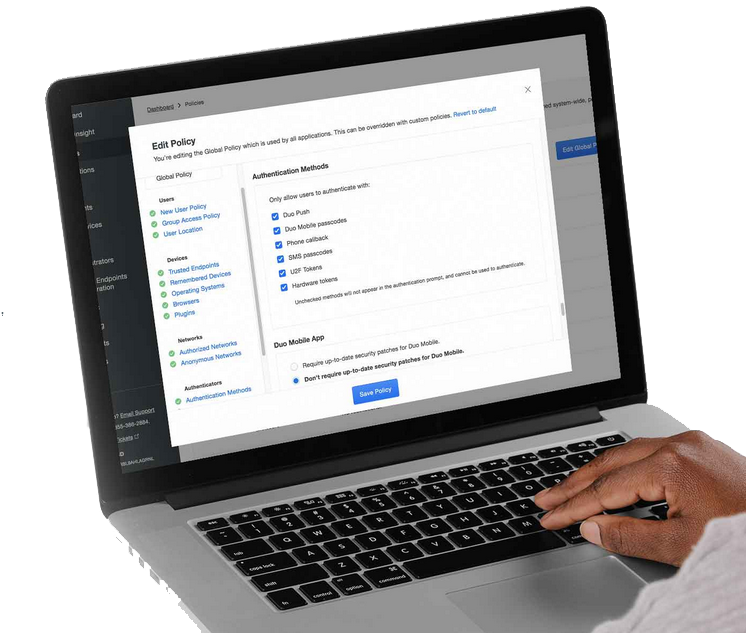
Adaptive Authentication & Policy Enforcement
Set & Enforce Adaptive User Policies
Want to grant access based on specific users or groups? How about by geolocation? Duo lets you set and enforce fine-grained policies to grant or block access attempts based on a user’s role, device hygiene, location, network and a host of other contextual factors. Determine who can access which applications based on an individual or group, or their specific roles and responsibilities. See where users are authenticating from and prevent unauthorized access from any geographic location.
- Control access based on network
- Block Tor and anonymous networks
- Set fine-grained device access policies
- Secure devices without an MDM
- Ensure healthy, updated devices
Remote Access & Single Sign-On
Secure Access to All Applications
Secure access boils down to one main goal: protect every application, whether it’s in the cloud or on-premises. With Duo’s remote access and single sign-on (SSO) you give your users secure access to all business applications, from any device and any location.
- Secure access to internal web applications
- Flexible, risk-based adaptive security policies to strengthen control
- Access to specific resources without a VPN
- Secure remote access to SSH
- Integrate with remote access providers
- Protect all applications (secure access to cloud apps/secure access to on-premises apps/natively protect all cloud apps/protect federated cloud apps)



