We all know the internet is a fantastic world of learning and entertainment for kids, but, like the real world, there can be dangers, too. With some precautions, you can…
Author: Editor

Understanding the Updated NIST Cybersecurity Framework
What It Means for BusinessesIn today’s increasingly digital world, businesses must stay ahead of the ever-growing threat landscape. Cyberattacks are becoming more sophisticated, and with the rise of remote work,…

Beware! Fake Funeral Livestream Scam
Cybercriminals are always finding new ways to exploit vulnerable situations, and sadly, the loss of a loved one is no exception. In this week’s alarming scam, hackers are targeting grieving…

Citynet Announces Promotion of Todd Dlugos to Chief Operating Officer (COO)
BRIDGEPORT, WEST VIRGINIA, USA, August 28, 2024 /EINPresswire.com/ — Today, Citynet President and CEO Jim Martin announced the promotion of Todd Dlugos, Citynet’s Chief Financial Officer, to the additional Chief…

Citynet Announces Dedication Event for New Fiber Broadband Network in Wetzel County, West Virginia
View Photo Gallery Wetzel County, WV – August 16, 2024 – Citynet is excited to announce the official dedication of its new fiber broadband network in Wetzel County, West Virginia.…
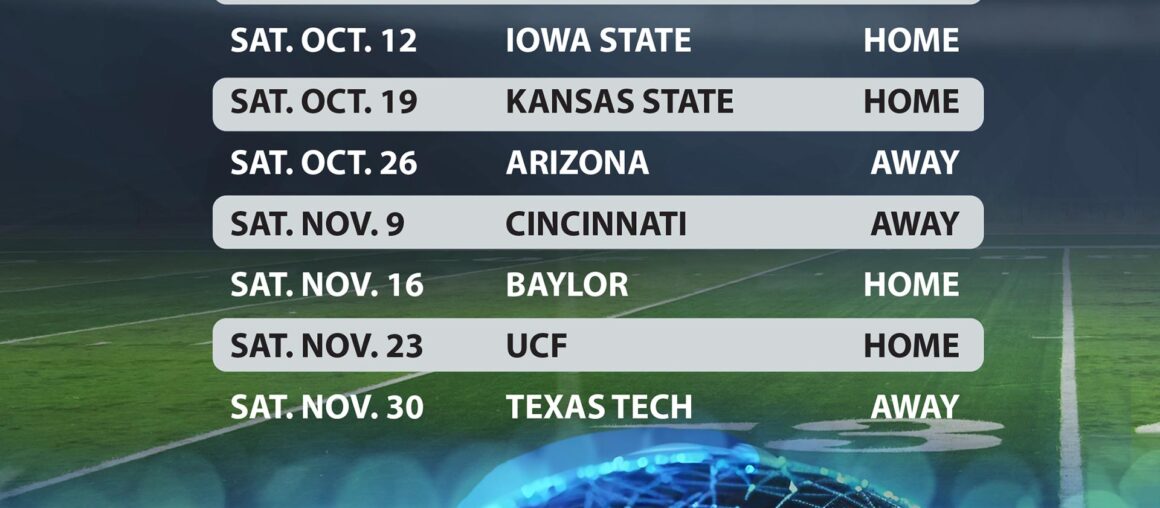
2024 Football Season is HERE!
And to celebrate, Citynet is offering a West Virginia University football schedule for convenient display on your smartphone! DOWNLOAD IT! To install this schedule as a wallpaper on a smartphone…

Understanding the Basics of Zero Trust
Why It’s Essential for Modern Cybersecurity In today’s digitally-driven world, the traditional perimeter-based security model is no longer sufficient. With the rise of remote work, cloud services, and sophisticated cyber…

The Five Biggest Cloud Security Threats
(And how to deal with them) Cloud computing has transformed business operations by enabling remote storage of data and applications, boosting agility and efficiency. However, this shift also brings potential…

5 Signs of Social Engineering
Legitimate emails can exhibit these traits, but messages with three or more of them are at a higher risk of being part of a social engineering attack. Most social engineering…

TOAD Attack
What is a TOAD Attack? A TOAD attack, which stands for Telephone-Oriented Attack Delivery, is a relatively new type of phishing attack that combines voice and email phishing techniques. In…




