Cybercriminals never stop devising new tricks, and one of their latest is so convincing that it can fool even the savviest internet users. It’s called a Browser-in-Browser attack (or BiB attack), and if you’ve ever clicked a login pop-up while signing into a website, you could be a target.
What is a Browser-in-Browser Attack?
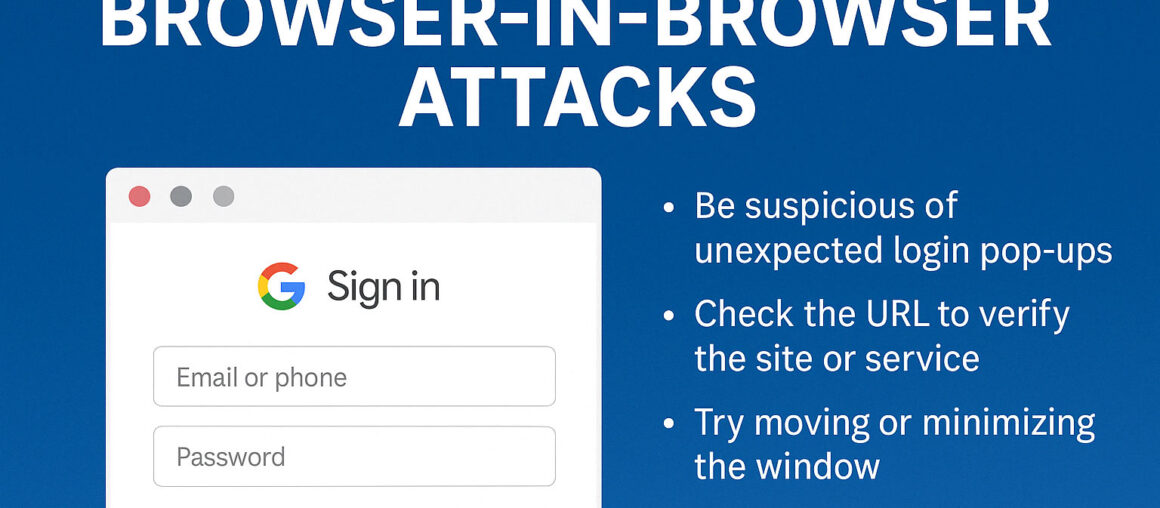
Many websites let you log in using a service like Google, Microsoft, or Facebook. You click a button, a login pop-up appears, and you type in your password. Simple, right?
But with a Browser-in-Browser attack, that login window isn’t real; it’s a fake window designed to look exactly like the real thing. The attacker builds a lookalike login box directly inside the web page, tricking you into entering your real credentials.
Once you hit “Submit,” your login details are instantly sent to the attacker, giving them access to your account.
How Can You Tell If a Pop-Up Window Is Fake?
Detecting a BiB attack takes a sharp eye, but these signs can help:
- Examine login windows closely
If the design, wording, or layout looks even slightly off, pause. Something may be wrong. - Test the window’s behavior
Try to resize, minimize, or drag the window off your screen. If it doesn’t behave like a normal browser pop-up, it may be a fake. - Check the URL
Real login windows come from the official site. If you’re unsure, open a new browser tab and log in directly; never trust a pop-up you weren’t expecting.
How to Stay Protected
- Use Multi-Factor Authentication (MFA)
MFA adds an extra step to your login process, making it much harder for attackers to break in, even if they steal your password. - Avoid third-party logins
It may be convenient to sign in with your Google or Facebook account, but it creates a single point of failure. If one account is compromised, everything connected to it is at risk. - Use a password manager
A password manager can help you create and store strong, unique passwords for every site and app, without having to remember them all. - Never reuse passwords
Repeating the same password across sites is risky. One breach can give attackers access to your entire digital life. - Keep your software up to date
Browser and OS updates often include critical security patches that help protect against attacks like BiB.
Stay Sharp, Stay Safe
Browser-in-Browser attacks are clever, convincing, and becoming more common. But with awareness and a few smart habits like using strong, unique passwords and avoiding third-party logins, you can stay one step ahead.
At Citynet, we don’t just connect you, we help protect you. Whether you’re a home user or running a business, we’re here with real solutions to keep your digital life secure.









 Huntress is a powerful cybersecurity platform designed to detect and respond to persistent threats that evade conventional security measures. It continuously monitors your IT environment, identifying hidden footholds, unauthorized access, and malware that could compromise your business. With its managed detection and response (MDR) capabilities, Huntress ensures that your organization is protected 24/7.
Huntress is a powerful cybersecurity platform designed to detect and respond to persistent threats that evade conventional security measures. It continuously monitors your IT environment, identifying hidden footholds, unauthorized access, and malware that could compromise your business. With its managed detection and response (MDR) capabilities, Huntress ensures that your organization is protected 24/7.










