
Stay Ahead of Cyber Threats with Citynet & Huntress
Cybersecurity threats are evolving at an alarming rate, and businesses of all sizes must remain vigilant against cybercriminals who are constantly looking for vulnerabilities to

Tips for Staying Alert Against Cyber Threats
Cybercriminals are constantly evolving their tactics to trick you into revealing sensitive information or compromising your security. Take a moment to review these key security

Protecting Your Personal Information on Your Smart TV
Smart TVs have become a staple in many homes, offering convenient access to streaming services, apps, and even smart home integrations. However, just like your

Citynet is Now a Cisco Certified Calling Provider – Seamlessly Manage Your Phone Services in Webex
At Citynet, we are always looking for ways to enhance the way businesses communicate. We’re excited to announce that Citynet is now a Cisco Certified

Organizations Observed 50% Increase in Deepfakes and Phishing Scams in 2024
Cybercriminals upped their game in 2024, using increasingly advanced tactics like AI-generated deepfakes and highly personalized phishing attacks. According to a recent report from AuthenticID,

Be Prepared for Storms!
Storms are bound to knock out power and the internet from time to time. Lightning strikes and power surges can easily damage your technology. Overnight

Citynet Announces $24.87 Million Investment to Expand GIG Fiber Network in Nicholas County Through ReConnect Program
Bridgeport, WV — Citynet, in partnership with the Nicholas County Commission and the U.S. Department of Agriculture (USDA) ReConnect Program, is proud to announce a
A Technology Checklist for SMBs: Weekly, Quarterly, and Annual Tasks for a Secure and Productive Year
The start of a new year is a great opportunity for small and medium-sized businesses (SMBs) to streamline operations and enhance cybersecurity. By following a

A Smart Tech Checklist for a Great New Year: Weekly, Quarterly, and Annual Tasks
As we welcome the new year, it’s the perfect time to get your digital life in order. With just a little planning, you can make
Power Cycling Your Router
It is important to have a good grasp of how your router works, as it can impact your wireless connectivity. If you are experiencing problems

Beware of the “Unsolicited Package Scam”
A New QR Code Scheme Targeting Victims In the fast-paced world of online shopping, receiving packages is a common occurrence. However, scammers have found a

CitynetTV & Internet Tip Sheet
TV REMOTE How to Reprogram Your Citynet Remote to Your TV Step 1: Press and hold the ‘setup’ button at the top right of your

Beware of Fake TSA PreCheck Emails
Travelers rely on TSA PreCheck to breeze through airport security. This U.S. airport screening program streamlines the security process, allowing members to avoid long lines

TIME TO GET SERIOUS: Digital Disaster Preparedness for Your Business
The Importance of Data Backup and ProtectionData is your business’s lifeblood, and it’s critical to ensure it’s protected. A robust data backup strategy ensures that

Prepare for Digital Disasters
Why Digitize Your Important Documents and Photos?Losing treasured family photos, tax records, or legal documents in a flood or fire is heartbreaking. Luckily, we live

Raising Digital Citizens
We all know the internet is a fantastic world of learning and entertainment for kids, but, like the real world, there can be dangers, too.

Understanding the Updated NIST Cybersecurity Framework
What It Means for BusinessesIn today’s increasingly digital world, businesses must stay ahead of the ever-growing threat landscape. Cyberattacks are becoming more sophisticated, and with

Citynet Announces Promotion of Todd Dlugos to Chief Operating Officer (COO)
BRIDGEPORT, WEST VIRGINIA, USA, August 28, 2024 /EINPresswire.com/ — Today, Citynet President and CEO Jim Martin announced the promotion of Todd Dlugos, Citynet’s Chief Financial

Citynet Announces Dedication Event for New Fiber Broadband Network in Wetzel County, West Virginia
View Photo Gallery Wetzel County, WV – August 16, 2024 – Citynet is excited to announce the official dedication of its new fiber broadband network
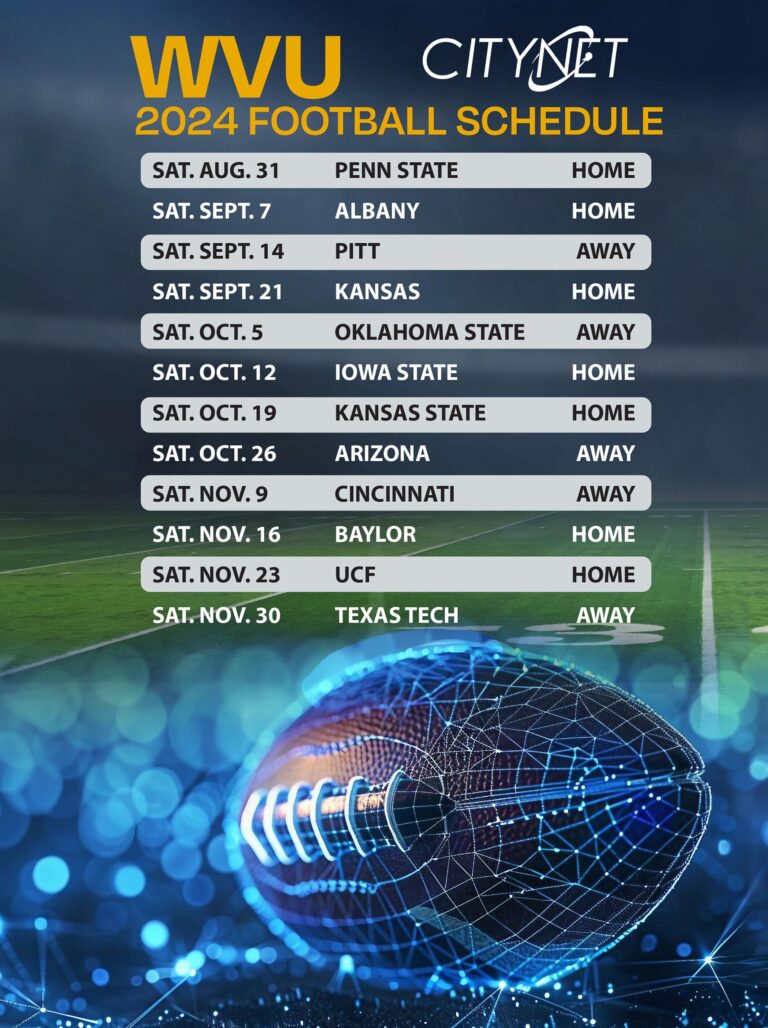
2024 Football Season is HERE!
And to celebrate, Citynet is offering a West Virginia University football schedule for convenient display on your smartphone! To install this schedule as a wallpaper

Understanding the Basics of Zero Trust
Why It’s Essential for Modern Cybersecurity In today’s digitally-driven world, the traditional perimeter-based security model is no longer sufficient. With the rise of remote work,

The Five Biggest Cloud Security Threats
(And how to deal with them) Cloud computing has transformed business operations by enabling remote storage of data and applications, boosting agility and efficiency. However,

5 Signs of Social Engineering
Legitimate emails can exhibit these traits, but messages with three or more of them are at a higher risk of being part of a social

TOAD Attack
What is a TOAD Attack? A TOAD attack, which stands for Telephone-Oriented Attack Delivery, is a relatively new type of phishing attack that combines voice



