What is a TOAD Attack?
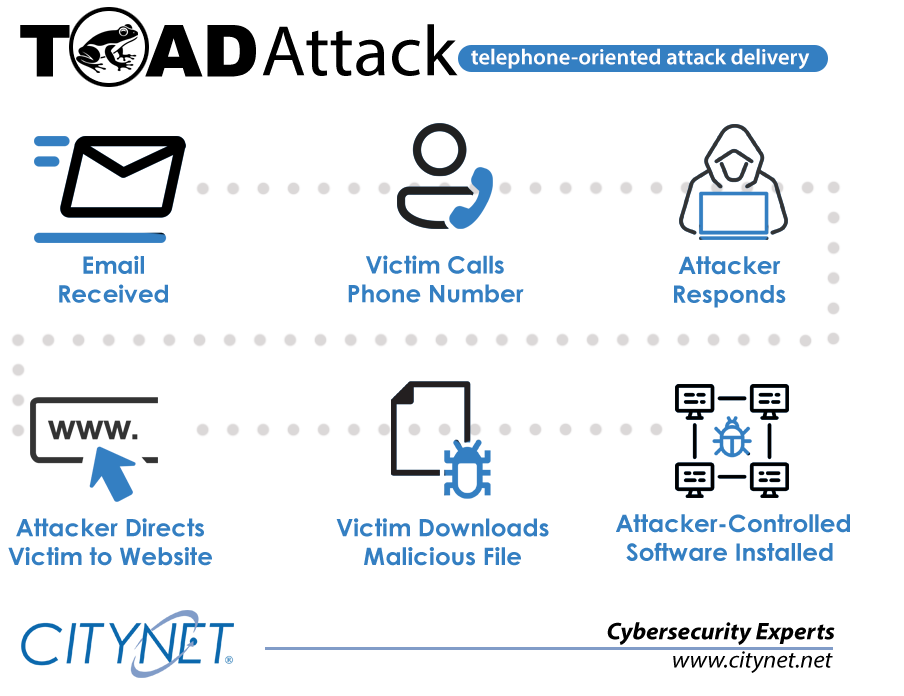
A TOAD attack, which stands for Telephone-Oriented Attack Delivery, is a relatively new type of phishing attack that combines voice and email phishing techniques. In this attack, cybercriminals impersonate a trusted authority figure to deceive users into revealing sensitive information, such as login credentials or financial data, over the phone.
The process typically involves the attacker calling the victim and claiming to be a representative from a reputable company or organization. Following the call, the attacker sends an email containing a phishing link or attachment. This multi-layered approach often includes elements like text or instant messages (smishing) and social engineering tactics to trick users into disclosing proprietary, personal, or financial data.
How Does TOAD Work?
TOAD attacks typically unfold in several stages:
1. Initial Phishing Email
The attacker sends a well-crafted phishing email to the target. This email may appear to come from a trusted source, such as a colleague, financial institution, or service provider. It aims to elicit a response or action from the target.
2. Information Gathering
Once the target responds to the email, the attacker gathers information from the interaction. This may include login credentials, personal details, or other sensitive information.
3. Follow-Up Phone Call
Using the information obtained, the attacker makes a phone call to the target. During this call, they use social engineering tactics to further manipulate the victim. They might pose as a technical support agent, bank representative, or another trusted entity.
4. Exploitation
The goal of the phone call is to extract additional sensitive information, install malware, or convince the victim to perform actions that compromise their security, such as transferring money or divulging confidential information.
Why TOAD is Effective
TOAD attacks are effective for several reasons:
1. Personalization
By combining email and phone interactions, attackers can create highly personalized and convincing scenarios. This increases the likelihood that the target will trust the attacker and comply with their requests.
2. Human Element
The use of social engineering over the phone exploits the human element of cybersecurity. People are often more trusting and less cautious when speaking with someone they believe to be legitimate.
3. Difficulty in Detection
Traditional email security solutions may detect and block phishing emails, but they are less effective at addressing the follow-up phone calls. This multi-channel approach makes TOAD attacks harder to identify and prevent.
Defending Against TOAD Attacks
To protect against TOAD attacks, organizations need to adopt a comprehensive and proactive approach to cybersecurity:
1. Employee Training
Educate employees about the dangers of TOAD attacks and the tactics used by attackers. Regular training can help staff recognize phishing emails and suspicious phone calls.
2. Advanced Email Security
Implement advanced email security solutions that use AI and machine learning to detect and block phishing attempts before they reach users’ inboxes.
3. Multi-Factor Authentication
Use multi-factor authentication (MFA) to add an extra layer of security to sensitive accounts. Even if attackers obtain login credentials, MFA can prevent unauthorized access.
4. Incident Response Planning
Develop and regularly update an incident response plan that includes procedures for dealing with TOAD attacks. Ensure that employees know how to report suspicious emails and phone calls.
5. Continuous Monitoring
Employ continuous monitoring solutions to detect and respond to suspicious activity in real time. This includes monitoring for unusual login attempts and network behavior.
How Citynet Managed Services Can Help
Citynet Managed Services offers comprehensive cybersecurity solutions to protect against TOAD attacks and other emerging threats:
1. Security Awareness Training
We provide training programs to educate your staff about the latest cyber threats and how to recognize them, reducing the risk of successful social engineering attacks.
2. Advanced Threat Detection
Our email security solutions leverage AI and machine learning to identify and block phishing emails before they reach your employees.
3. Incident Response Support
Our team of experts can assist with developing and implementing an incident response plan tailored to your organization’s needs.
4. Continuous Security Monitoring
Citynet offers continuous monitoring services to detect and respond to suspicious activity in real-time, ensuring that threats are addressed promptly.
At Citynet, we are committed to helping organizations navigate the complex world of cybersecurity. Contact us today to learn more about our services and how we can help you defend against TOAD attacks and other advanced threats.