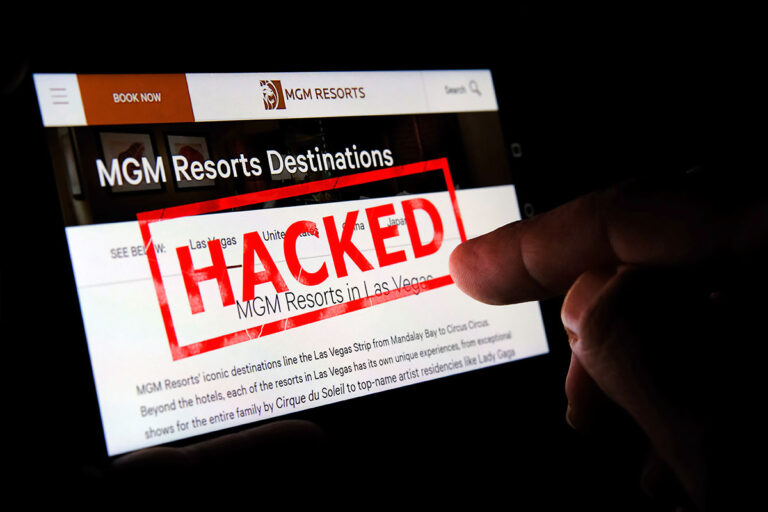
MGM Resorts International, a major hospitality and entertainment company, was recently the victim of a cyberattack that cost the company over $52 million in lost revenue as nearly all of MGM’s hotels, casinos, and ATMs went offline. The attack started with a simple social engineering scam using LinkedIn, in which a cybercriminal impersonated an MGM employee and called the IT department to reset their password. This gave the cybercriminal access to the employee’s account and eventually led to the cybercriminal taking over MGM’s entire system.
This attack is a reminder that cybercriminals are constantly looking for new ways to exploit businesses and individuals. It is essential to be vigilant and protect yourself from similar attacks.
Here are some tips to stay safe from social engineering scams:
- Be careful with the information you share about yourself online. Cybercriminals can use this information to target you in phishing attacks.
- Confirm that the person you’re speaking to is actually who they say they are. Try reaching out to them using another form of contact or by meeting with them face-to-face.
- Be suspicious of emails, texts, and social media posts that contain shocking information about this event. These may lead to disinformation, which is false information designed to mislead you.
Here are some additional tips to protect your business from cyberattacks:
- Implement a strong security policy and train your employees to identify and avoid cyber threats.
- Use strong passwords and multi-factor authentication for all of your accounts.
- Keep your software up to date with the latest security patches.
- Have a backup and recovery plan in place in case of a cyberattack.
By following these tips, you can help protect yourself and your business from cyberattacks.
The best way to train employees – and test them – on how to avoid the latest network security traps set by cybercriminals is with security awareness training from Citynet partner KnowBe4. Contact us today to learn more about this dynamic solution that should be a critical component of your network security strategy.