Artificial intelligence (AI) has become increasingly popular in the past year. Many people have started using AI chatbots like ChatGPT or Google Bard. Unfortunately, cybercriminals are taking advantage of AI’s…
Year: 2023

Safe Digging!
Did you know that April is Safe Digging Month? Warm days have arrived! Before digging post holes, planting trees, or doing any other chore that requires digging, ALWAYS call WV811…

Cybersecurity on a Small Business Budget
Your guidebook on how to secure your business in minutes Just because you’re a small business doesn’t mean you won’t be a target for cyberattacks. In fact, small businesses can…

Hovering Over Links
How can you tell if an email is safe? Even if you catch red flags in an email, such as typos or poor grammar, an urgent demeanor, or even a…

Real Products, Fake Payments
Recently, the US FBI has issued a warning about business email compromise (BEC) attacks by cybercriminals, who are trying to steal physical goods. BEC is when cybercriminals spoof business email…

Watch Out for Silicon Valley Bank Scams
Recently, the US-based Silicon Valley Bank (SVB) recently shut down due to failure to meet its financial obligations. This collapse has caused a public panic, and unfortunately, cybercriminals take advantage…
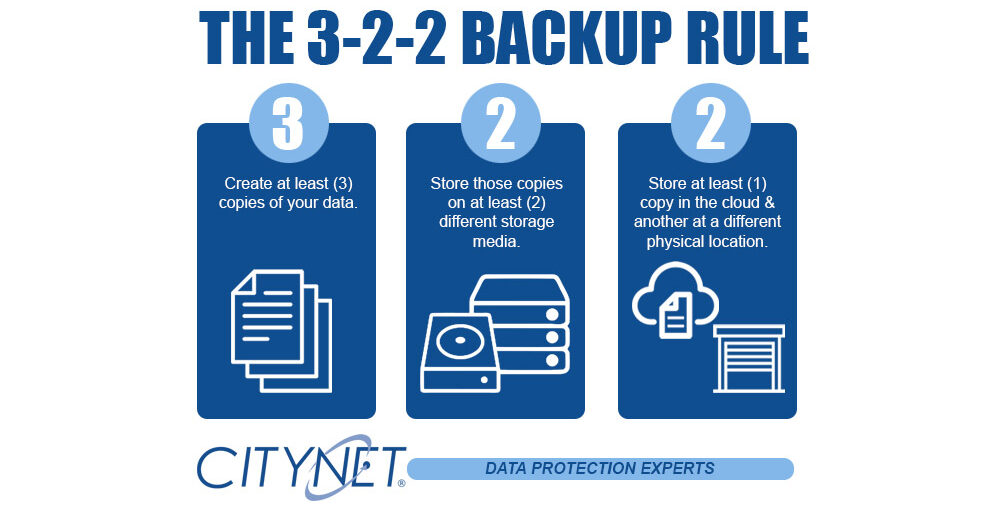
The 3-2-2 Backup Rule
What if you lose critical data during a disaster? It’s scary to think about, but something every business (and individual!) must plan for in order to mitigate any damage from…
New Alert! Cybercriminal at Your Door
Ring is a popular brand of security cameras designed for home safety. Unfortunately, Ring customers were the latest victims of a phishing attack. Cybercriminals sent phishing emails spoofed as Ring…

Hiding Behind Namecheap
he web hosting company Namecheap was the latest victim of a combined hacking and phishing attack. In this attack, cybercriminals hacked into SendGrid, Namecheap’s email service. Then, they used SendGrid…

Video Game Scams
Video games are a popular pastime for people across the world. Even if you’ve never played video games, you’ve probably heard of games like Legend of Zelda, Minecraft, FIFA, or…




